Data & Security
1. Introduction
We are committed to protecting your data and ensuring your information is handled with the highest security standards. Our infrastructure, practices, and partners (like Microsoft Azure and Stripe) meet or exceed industry best practices.

SoftTrain Cloud Ltd is registered with the Information Commissioner's Office (ICO).
Registration reference: ZB520371
Click here for details of the registration.
2. Infrastructure & Hosting (Powered by Azure)
Our applications are hosted on Microsoft Azure’s secure cloud infrastructure. Azure provides robust security controls, including DDoS protection, network isolation, and compliance certifications such as ISO 27001, SOC 2, and GDPR.

Access restrictions
Access is limited to the SoftTrain Cloud Technical Support Team using the built-in Azure Network Security Group which restricts ports and IP access. Only port 443 (https) is open to public access (as is required to run a web application), all other limited administrative ports are restricted by remote IP access and only for ports required to perform Technical Support duties.
Connections to the SQL database for Technical Support are encrypted as per the Microsoft guidance.
Connectivity to the Azure cloud configuration is limited to the SoftTrain Cloud Technical Support Team and uses a combination of username, password and the Microsoft Authenticator App for authentication.
Product File Storage
For any SoftTrain Cloud product requiring secure file storage (for example: Call Recording Archive), the files are stored on the Azure Blob Storage.
File encryption
Call recording files are collected from the PBX and encrypted using Rijndael AES encryption using a combination of password, secret key and initialisation vector. Once encrypted they are uploaded to the Microsoft Azure Blob Storage service.
File Storage
The encrypted call recording files are stored on the Microsoft Azure Blob Storage service using Read-access geo-zone-redundant storage (RA-GZRS). Full details of the storage mechanism can be found on the following URL:
https://learn.microsoft.com/en-us/azure/storage/common/storage-redundancy
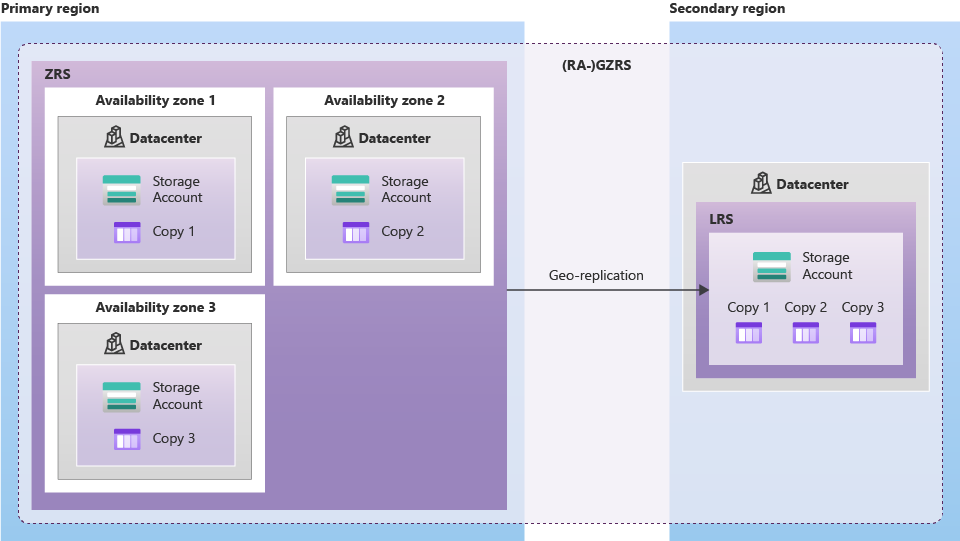
File access restrictions
By default, the storage containers hosting the call recordings are disabled to all access excluding the following:
- Analytics Web Interface (via server-server Rest API restricted by Azure application).Access permissions to files are controlled by the Administrator(s) of the Analytics Web Interface or by a SuperUser who has been granted full access by the Administrator.
- SoftTrain Cloud Azure Administrators
Below is a screenshot of the access permissions defined in the Microsoft Azure Blob Storage service:
Are all critical information assets located in a physically secure area? | YES |
How are systems protected from environmental hazards such as fire, smoke, water, vibration, electrical supply interfaces, and dust? | |
Fire suppression systems installed in server rooms/data centres? | |
What exterior security is provided ? | Azure facilities, premises and physical security |
3. Data Protection & Encryption
All passwords are encrypted using industry-standard AES-256 encryption at rest and TLS 1.2+ in transit. Access to production data is strictly limited.
4. Application & Operational Security
Application Security
User logins are authenticated via username and password and using Multi-Factor Authentication (MFA) by emailing a code to the users email account. There is the option to trust the device for a period of 90 days where the MFA code will not be required for subsequent logins on the same device.
SoftTrain Cloud responsibility
The initial login to the portal is provided by SoftTrain Cloud to the Reseller and with controls to manage the end-client logins.
Reseller responsibility
The Resellers are responsible to ensure their end-clients are correctly provisioned subject to the Terms & Conditions agreed by the Reseller.
Operational Security
Our operational security controls are designed to minimize risk, enforce accountability, and ensure secure management of the platform across the entire software delivery lifecycle.
1. Access Control & Authentication
- Role-Based Access Control (RBAC) is implemented across systems and services.
- Access to production infrastructure is limited to SoftTrain Cloud Technical Support team.
- All privileged access requires Multi-Factor Authentication (MFA) via the Microsoft Authenticator App.
- Access permissions are reviewed periodically and revoked immediately upon role changes or termination.
2. Secure Development & Deployment
- Code is deployed through a two-stage process: 1. Pre-production release environment for verification. 2. Automated QA pipeline for integration and functional testing
- Changes are committed via version-controlled repositories (Git), and deployment to production is automated
- Deployment artifacts and infrastructure changes are logged
3. Monitoring, Alerts & Incident Handling
- Real-time infrastructure and application monitoring is in place.
- System and error alerts are automatically sent via: Email (for critical issues) and Slack (for operational visibility and rapid response)
- A basic incident response workflow is documented and executed by the core technical team upon detection of anomalies.
4. Credential & Identity Security
- Password policies enforce: Minimum length: 8 characters; Complexity: Uppercase, lowercase, number, and symbol required
- MFA is mandatory for all users with infrastructure-level access.
- Administrative credentials are restricted to designated personnel.
5. Employee Onboarding & Offboarding
- Administrative and infrastructure access is provisioned only on a need-to-know basis.
- Offboarding includes immediate revocation of access rights, device checks, and audit log review.
- Security responsibilities are reviewed during onboarding for technical staff.
6. Workstation & Device Security
- All employee workstations are configured with automatic screen locks that activate after a brief period of inactivity.
6. Third-Party Access
- No third-party vendors or contractors are granted direct access to production systems or customer data.
- All third-party integrations operate via secure APIs or SDKs, with scoped permissions where applicable.
How often are security policies reviewed and updated? | Annually or as required based on changes in the security landscape or organizational needs |
Who is responsible for the security policy development, maintenance, and issuance? | Technical Director |
Are all security policies and standards readily available to all users? | YES |
Are security policies available for review? | YES |
| Is incoming traffic scanned for viruses? | YES |
| How is system documentation secured from unauthorised access? | Stored on Azure file share with limited access and via password protected management tools |
| Are backup procedures documented and monitored? | YES |
5. Authentication & Account Security
- Multi-factor authentication (MFA)
- SSO integration with Microsoft
- Password complexity: Minimum 8 characters including uppercase and lowercase letters, numbers and symbols
- Session management via secure, http-only, host-only cookies
6. Payment Security (Powered by Stripe)
We use Stripe, a PCI DSS Level 1 certified provider, for all payment processing. Your payment details never touch our servers.
Stripe hold reseller data only for billing purposes.
7. Incident Response & Reporting
Our team follows a documented incident response process to quickly identify, contain, and remediate security events. Critical incidents trigger immediate alerts to relevant personnel to minimize impact. We commit to transparent communication and timely updates to affected customers.
For detailed information on our incident handling timelines and support commitments, please refer to our Support SLA.
Appendix
Artificial Intelligence (AI) Products
The following products make use of Artificial Intelligence (AI):
- Call Recording AI - transcription of call recordings and sentiment rating of the call
- Live Chat & Chatbot - sentiment rating of the chat
For products making use of AI, the security of the data is determined by the AI engines used. Details of these can be found behind the following links:
Azure Speech-to-text
Open AI Chat Completions
AI data at rest
Once the data from the AI APIs are returned to SoftTrain Cloud, the transcriptions are stored in the SQL database in a format suitable to allow text searching from the Analytics tool. Sentiment rating is stored as a single integer (1-5) relating to the sentiment value determined by the Chat Completion API.
Last updated: 4 July 2025